
Does Verizon have a security flaw? This is a question we'll attempt to answer after a tip was received today claiming a possible 'backdoor' in Verizon's FiOS wireless internet service.
The claim stated that the security in Verizon's FiOS (Fiber Optic Services) router can be easily bypassed. What exactly does this mean? The wireless SSID (indentifier) and settings can be obtained with no security check. More importantly, the network encryption password is also attainable. That's right -- the 'secure' password can be easier to obtain than once thought. I decided to take a closer look into this claim.
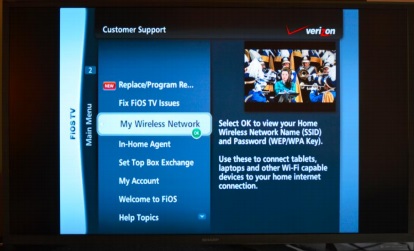 Needless to say, Verizon should revisit the security built into their system. Without any security checks to validate who
their customers are, pressing
MENU/CUSTOMER SUPPORT/WIRELESS SETTINGS on a FiOS customer's
remote displays the network name (SSID), encryption password (seen here), firewall settings, router settings (seen here), logs, advanced settings, and more.
No security check required, no PIN code – freely available to any baby-sitter, contractor, or domestic help.
Needless to say, Verizon should revisit the security built into their system. Without any security checks to validate who
their customers are, pressing
MENU/CUSTOMER SUPPORT/WIRELESS SETTINGS on a FiOS customer's
remote displays the network name (SSID), encryption password (seen here), firewall settings, router settings (seen here), logs, advanced settings, and more.
No security check required, no PIN code – freely available to any baby-sitter, contractor, or domestic help.
While some may downplay the threat stating the person attempting to obtain this information must obviously be locate in the house, think again.
I visited Verizon's website. From there you can check your account, pay a bill, send email - and retrieve wireless settings from the internet. Look how simple. Because I do not have Verizon FiOS, I tested just how easy it is to get wireless settings from someone other than myself. With permission from my father, a FiOS customer, I attempted to find some answers.
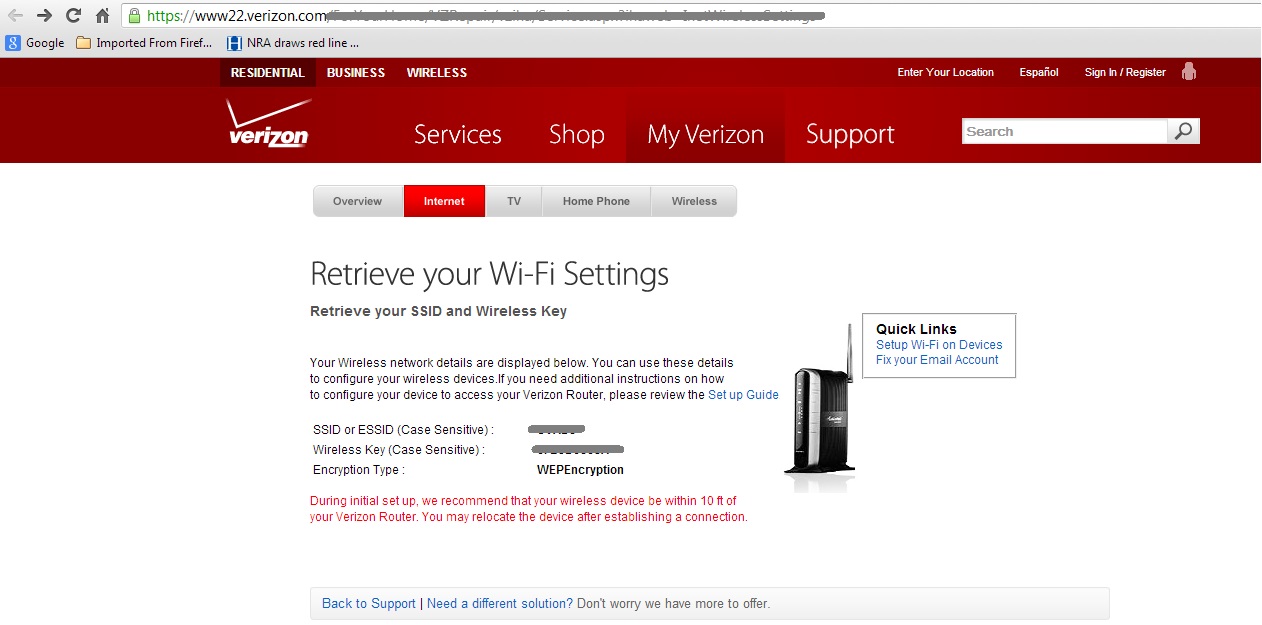 Verizon's web page prompts for two items to be granted access. These items are: (a) a valid Verizon phone number followed by (b) the amount of your monthly bill.
I first entered my father's phone number. Gaining access next requires validating who I am by entering the amount on my monthly bill.
Verizon's web page prompts for two items to be granted access. These items are: (a) a valid Verizon phone number followed by (b) the amount of your monthly bill.
I first entered my father's phone number. Gaining access next requires validating who I am by entering the amount on my monthly bill.
Hmmm...well that should not be too difficult - a little social engineering is all it would take for an attacker to obtain the amount on a bill.
Keep in mind, pricing for service is on the Verizon website.
It took little time to realize that calling Verizon from the phone of residence needs no authentication to review payment history. Don't believe me? Try it. I dialed 800-922-0204 and going through the menu options: #, 2, 1, 2, 1, 3 gave me a payment history with no validation of who I was!
Google is also amazing. I found my father's monthly bill amount is the same amount as many others, including the City of Fort Collins. Starting to get it yet? Not only residential household use FiOS - many local governments use the service as well, all of which have phone numbers. After entering the bill amount, I was granted access to my dad's account. On my screen was his SSID, encryption type and password (seen here).
Verizon's authorization from the internet is single factor authentication: 'Something you know', being telephone number and bill amount. And again, for any lobby visitor, home babysitter, contractor or anyone else for that matter, no authentication is needed - not even a PIN code.
Is this technically a 'backdoor' vulnerability? By definition, a backdoor is an undocumented way of gaining access. Are either of these methods undocumented? I took to the phone to call Verizon and speak with an agent about this. I attempted to call Verizon and bring this to their attention for commenting. The menu system is frustrating if you want to talk to a human. Good luck trying to contact them via the contact page. After struggling, I finally thought I was getting somewhere before I was disconnected. I called back a second time, navigated the menus for over 5 minutes before being disconnected once more.
I like Verizon. The company keeps Comcast out of my home. I just hope they take security more seriously and make changes to protect their customers.
I'll keep trying to get some answers and updates will be provided. In the meantime, for those concerned about security, a workaround is to disable the FiOS router wireless, and setup another wireless router behind it.
Updates to come...

